Cybersecurity Write for Us
 Cybersecurity Write for Us – Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks aim to access, modify or destroy confidential information, extort money from users via ransomware, or disrupt normal business processes.
Cybersecurity Write for Us – Cybersecurity is the practice of protecting systems, networks, and programs from digital attacks. These cyberattacks aim to access, modify or destroy confidential information, extort money from users via ransomware, or disrupt normal business processes.
How to Submit Article
To Submitting Your Articles, you can email us at contant@justtechweb.com
A strong cybersecurity strategy can provide a good security posture against malicious attacks designed to access, modify, delete, destroy, or extort an organization’s or user’s sensitive data and systems. Cybersecurity also plays a key role in preventing attacks aimed at disabling or disrupting the operations of a system or device. Implementing effective cybersecurity measures is incredibly challenging today as there are more devices than people, and attackers are increasingly innovative.
Why Is Cybersecurity Important?
 With an increasing number of users, devices and programs in the modern enterprise, combined with the growing deluge of data, most of which is sensitive or confidential, the importance of cybersecurity continues to grow. The ever-increasing number and sophistication of cyber attackers and attack techniques further compound the problem.
With an increasing number of users, devices and programs in the modern enterprise, combined with the growing deluge of data, most of which is sensitive or confidential, the importance of cybersecurity continues to grow. The ever-increasing number and sophistication of cyber attackers and attack techniques further compound the problem.
What are the Different Types of Cybersecurity?
Cybersecurity is a broad field spanning multiple disciplines. It can remain divided into seven main pillars:
1. Network Security – Cybersecurity Write for Us
Most attacks occur on the network, and network security solutions remain designed to identify and block these attacks. These solutions include data and access controls such as Data Loss Prevention (DLP), IAM (Identity Access Management), NAC (Network Access Control) and NGFW (Next-Generation Firewall) to enforce specific web usage policies.
2. Security in the Cloud – Cybersecurity Write for Us
As organizations increasingly adopt cloud computing, securing the cloud becomes a top priority. A cloud security strategy includes cybersecurity solutions, controls, policies, and services that help protect an organization’s entire cloud implementation—applications, data, infrastructure, etc.—against attacks.
3. Endpoint Security
The zero-trust security model prescribes the creation of micro-segments around data wherever it resides. Using endpoint security is one way to accomplish this with a mobile workforce. With endpoint security, businesses can protect end-user devices such as desktops and laptops with data and network security controls. Advanced threat prevention, such as anti-phishing and anti-ransomware, and technologies that provide forensics, such as endpoint detection and response (EDR) solutions.
4. Mobile Security
Often overlooked, mobile devices such as tablets and smartphones have access to corporate data, exposing businesses to threats from malicious apps, zero-day attacks, phishing and instant messaging (IM). Mobile Security prevents these attacks and protects operating systems and devices from rooting and jailbreaking. When combined with an MDM (Mobile Device Management) solution, enterprises can ensure that only supported mobile devices can access corporate assets.
5. IoT Security
While using Internet of Things (IoT) devices certainly brings productivity benefits, it also exposes organizations to new cyber threats. Threat actors seek out vulnerable devices that remain inadvertently connected to the Internet for malicious purposes, such as a path to a corporate network or another bot in a global botnet.
What are the Primary Cybersecurity Challenges?
 Cybersecurity remains continually challenged by hackers, data loss, privacy, risk management, and evolving cybersecurity strategies. The number of cyber attacks will not remain expected to decrease soon. In addition, the increase in entry points for attacks, such as with the advent of the Internet of Things (IoT), and the growing attack surface increase the need to protect networks and devices.
Cybersecurity remains continually challenged by hackers, data loss, privacy, risk management, and evolving cybersecurity strategies. The number of cyber attacks will not remain expected to decrease soon. In addition, the increase in entry points for attacks, such as with the advent of the Internet of Things (IoT), and the growing attack surface increase the need to protect networks and devices.
Ongoing challenges include evolving threats, data deluge, cybersecurity awareness training, labour shortages and skills gaps, and chain risks to vendors and third parties.
Evolving Threats
One of the most problematic elements of cybersecurity is the evolving nature of security risks. As new technologies emerge and remain used in new or different ways, new avenues of attack develop. Keeping abreast of these frequent changes and advances in attacks and updating practices to protect against them can be challenging. It can be especially difficult for small organizations without adequate staff and internal resources. The issues include ensuring that all cybersecurity elements are continuously updated to protect against potential vulnerabilities.
Data Deluge
Additionally, organizations can collect a large amount of potential data about people who use one or more of their services. With more data collected, the likelihood of a cybercriminal wanting to steal personally identifiable information (PII) is another concern. For example, an organization that stores PII in the cloud may be subject to a ransomware attack. Organizations should do everything in their power to prevent a cloud breach.
Cyber Security Awareness Training
Cybersecurity programs should also address end-user training. Employees can accidentally bring threats and vulnerabilities to their workplace on their laptops or mobile devices. Likewise, they may act in dangerous ways, such as clicking on links or downloading attachments from phishing emails.
Regular security awareness training will help employees do their part to protect their businesses from cyber threats.
How to Submit Article
To Submitting Your Articles, you can email us at contant@justtechweb.com
Why Write for Just Tech Web – Cybersecurity Write for Us
 Search Related Terms to Cybersecurity Write for Us
Search Related Terms to Cybersecurity Write for Us
Computer Systems
Networks
Software
Hardware
Data
Wireless Network
Television
IoT
Hand Bags
Stylish Bags
Sensors
Wireless Sensor Networks
Smart Devices
Digital Pay
Payment Service Provider
Computer
Laptop
Keyboard
Mouse
RAM
ROM
Mother Board
Technology News
Network Nodes
New Technology
Networking Hardware
Telecommunication Network
Internet Protocol
What is Technology
Network Topologies
Technology Definition
Digital Interconnections
Science and Technology
Latest Technology
Latest Technology News
Technology Review
Modern Technology
Technology Articles
Science Technology
Technology Meaning
Search Terms for Cybersecurity Write for Us
Write For Us
Looking For Guest Posts
Guest Posting Guidelines
Become A Guest Blogger
Writers Wanted
Guest Posts Wanted
Submit The Post
Contributing Writer
Guest Post
Becomes An Author
Suggest A Post
Contributor Guidelines
Guest Posts Wanted
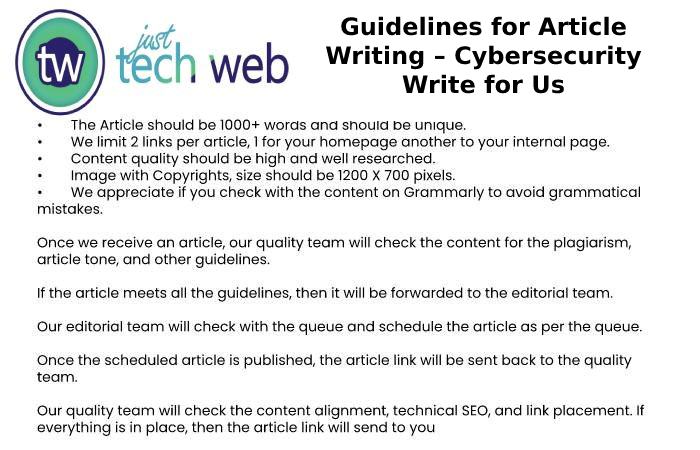
Guidelines for Article Writing – Cybersecurity Write for Us
 Related Pages
Related Pages
Blockchain Technology Write for Us
Content Marketing Write for Us
You can send your article to the contact@justtechweb.com

